¸¦µæ¥Æ¡¼¥Þ
Last-modified: 2014-02-27 (ÌÚ) 13:55:39
Top/¸¦µæ¥Æ¡¼¥Þ
¸¦µæ¥Æ¡¼¥Þ†
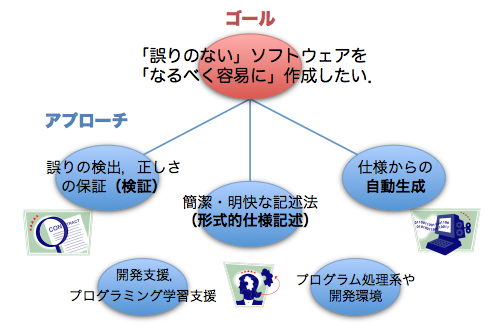
¡Ö¸í¤ê¤Î¤Ê¤¤¡×¥½¥Õ¥È¥¦¥§¥¢¤ò¡Ö¤Ê¤ë¤Ù¤¯Íưפˡ׺îÀ®¤¹¤ë¤¿¤á¤ÎÊýË¡¤Ë¤Ä¤¤¤Æ¸¦µæ¤·¤Æ¤¤¤Þ¤¹¡£Î㤨¤Ð¡¢
- ¥×¥í¥°¥é¥à¤Ë¸í¤ê¤¬¤Ê¤¤¤³¤È¤ò¤É¤¦³Î¤«¤á¤¿¤é¤è¤¤¤«?
- ¤ï¤«¤ê¤ä¤¹¤¤½ñ¤Êý¤Ç»ÅÍͤò½ñ¤±¤Ð¡¢¤¢¤È¤Ï¼«Æ°Åª¤Ë¥×¥í¥°¥é¥à¤òÀ¸À®¤Ç¤¤Ê¤¤¤«?¡Ê¤¢¤ë¤¤¤Ï¡¢¤Ê¤ë¤Ù¤¯´ÊÊؤÊÊýË¡¤Ç¥×¥í¥°¥é¥ß¥ó¥°¤Ç¤¤Ê¤¤¤«?¡Ë
¤È¤¤¤Ã¤¿ÌäÂê¤ËºÇ¤â¶½Ì£¤¬¤¢¤ê¤Þ¤¹¡£¡Ö¸¡¾Ú¡×¡Ö·Á¼°Åª»ÅÍ͵½Ò¡×¡Ö¼«Æ°À¸À®¡×Åù¤¬¥¡¼¥ï¡¼¥É¤Ç¤¹¡£
¼ÂºÝ¤Ï¡¢¥×¥í¥°¥é¥à¤Î¡ÖÀµ¤·¤µ¤òÊݾڤ¹¤ë¤³¤È¡×¡¢¥×¥í¥°¥é¥ß¥ó¥°¤Î¡ÖÍưײ½¡×¡Ö¼«Æ°²½¡×¡¢¤Ê¤É¤Ë´Ø·¸¤¹¤ë¤³¤È¤ÏÉý¹¤¯²¿¤Ç¤â¸¦µæ¥Æ¡¼¥Þ¤Î¸õÊä¤È¹Í¤¨¤Æ¤¤¤Þ¤¹¡£
´¶ÈÏÀʸ†
¼ç¤Ê³Ø³°È¯É½†
- Lamilla Alvarez & Takata. A formal verification of a subset of information-based access control based on extended weighted pushdown system, IEICE Trans. Inf. & Syst., E97-D(5), 2014, to appear.
- Lamilla Alvarez & Takata. An HBAC-based approximation for IBAC programs, SIN 2013, 277--281.
- Takata & Seki. Automatic generation of history-based access control from information flow specification, ATVA 2010, Lecture Notes in Computer Science 6252, 259--275.
- Takata & Seki. Formal language theoretic approach to the disclosure tree strategy in trust negotiation, IEICE Trans. Inf. & Syst., E92-D(2), 200-210, 2009.
- ¹âÅÄ, ²¦, ´Ø. ¼Â¹ÔÍúÎò¤Ë´ð¤Å¤¯¥¢¥¯¥»¥¹À©¸æ¤Î·Á¼°¥â¥Ç¥ë¤È¸¡¾Ú, ¿®³ØÏÀD, J91-D(4), 847-858, 2008.
- Yagi, Takata, & Seki. A labeled transition model A-LTS for history-based aspect weaving and its expressive power, IEICE Trans. Inf. & Syst., E90-D(5), 799--807, 2007.
- Yagi, Takata, & Seki. A static analysis using tree automata for XML access control, ¥³¥ó¥Ô¥å¡¼¥¿¥½¥Õ¥È¥¦¥§¥¢, 23(3), 51--65, 2006.
- ¹âÅÄ, Ãæ¼, ´Ø. XMLʸ½ñ¤ËÂФ¹¤ë¥¢¥¯¥»¥·¥Ó¥ê¥Æ¥£¥¬¥¤¥É¥é¥¤¥óŬ¹çÀ¸¡¾Ú, ¿®³ØÏÀD, J89-D(4), 705--715, 2006.